It goes without saying that you should change your passwords immediately. Do you use the same password for multiple things? If so, stop that.
Ask Lemmy
A Fediverse community for open-ended, thought provoking questions
Rules: (interactive)
1) Be nice and; have fun
Doxxing, trolling, sealioning, racism, and toxicity are not welcomed in AskLemmy. Remember what your mother said: if you can't say something nice, don't say anything at all. In addition, the site-wide Lemmy.world terms of service also apply here. Please familiarize yourself with them
2) All posts must end with a '?'
This is sort of like Jeopardy. Please phrase all post titles in the form of a proper question ending with ?
3) No spam
Please do not flood the community with nonsense. Actual suspected spammers will be banned on site. No astroturfing.
4) NSFW is okay, within reason
Just remember to tag posts with either a content warning or a [NSFW] tag. Overtly sexual posts are not allowed, please direct them to either !asklemmyafterdark@lemmy.world or !asklemmynsfw@lemmynsfw.com.
NSFW comments should be restricted to posts tagged [NSFW].
5) This is not a support community.
It is not a place for 'how do I?', type questions.
If you have any questions regarding the site itself or would like to report a community, please direct them to Lemmy.world Support or email info@lemmy.world. For other questions check our partnered communities list, or use the search function.
6) No US Politics.
Please don't post about current US Politics. If you need to do this, try !politicaldiscussion@lemmy.world or !askusa@discuss.online
Reminder: The terms of service apply here too.
Partnered Communities:
Logo design credit goes to: tubbadu
And use a password manager like Bitwarden
Bitwarden and Bitwarden Authenticator are the GOATs.
If you pay for bitwarden or self-host the normal app can also be an authenticator, with the added ability to sync the codes.
Bitwarden is awesome! I used it for like three years, but I recently moved everything to Keepass. Only thing with Keepass is having to manage your own backups
Why did you move to KeePass? I host my own vaultwarden instance for myself and my friends.
I wanted to try something new and I also figure it's a bit more future-proof in case Bitwarden ever decides to change their pricing models such that the free tier loses any features.
I'm sure self-hosting your password manager gives you some awesome bonuses but I don't have the knowhow nor do I have control over the family internet router so I don't think I can work that out just yet.
why did you change? bitwarden is the best, what benefit did you gain? also sounds way cooler than keepass
Bitwarden is great because they're convenient. However, I figure that becoming self-reliant on maintaining my own password database wouldn't be a bad idea. I believe storing everything locally gives me just a tad more security in case something were to happen with Bitwarden.
You could self-host vaultwarden
I've not got the knowhow to do that. I'm also not in charge of the family router so I haven't got the permissions to really manage my own server anyway. Someday I'll have my own place and I'll probably put something together but I'm pretty satisfied with Keepass :)
Makes sense, if you ever need help with self hosting you can DM me on Matrix. The address is on my profile description.
Password reuse is a real mother fucker. Good luck.
To add on, it sounds like you were phished. No shame, it happens to everyone. The best course of action when you get an email like that, DONT click the easy to press recover account button in the email. Always go directly to the site, even if the email looks legit.
From there you entered your password into, what im assuming, was a fake Macys website, where you gave the bad actors the exact info they needed to really activate it.
This sounds like EXACTLY what happened.
To add on to everyone else mentioning it, another benefit to password managers is that they auto filter themselves to the URL. So if you have a password saved for macys.com and get phished to macys-passwordreovery.com, the password manager won't know the URL and offer no filtering. Adding the extra step of having to manually find your password entry should be a flag itself that something might be wrong.
Firstly, probably remove the address from the OP. Don't want any Lemmy vigilantes getting involved and making a mess of things.
If you have 2fa enabled, you should be good. Even if they do guess your password, they shouldn't* be able to log in to your account. Although might still be worth making sure you have a nice strong password anyway. Also, if you have recovery phone numbers or email addresses attached to your email account, make sure they're secured as well.
* Assuming that your webmail provider is doing everything correctly, which isn't always a given if they're a small one.
I'm okay with the attacker's IP being public domain
You're assuming that the attacker is using their own IP rather than a compromised system owned by someone else.
Likewise, they might be using someone else's address with the intent to steal a package from their porch or something.
It'd be rather silly for a theif to use their own details.
These losers train each other to try to remote desktop into victims’ machines.
OP probably also needs to secure their mobile account, since the attacker could redirect recovery or MFA SMSs to their own number.
Check if your email service has an option to log off from all devices first. This will close any active sessions and prevent anyone that might be already logged in to do anything without logging in again.
Then change your password.
If you have 2FA, try to use something like an authenticator app instead of a cell phone number to receive an SMS message. Sim cards can be cloned. Authenticator apps can't.
It's worth noting that the option to log out all devices sometimes doesn't happen immediately. Microsoft's 365, for example, isn't immediate for all devices. If a massive player doesn't behave the way a user might expect, that's indicative of how chaotic the landscape can be. Good luck!
Are you also getting a bunch of random "confirm your email address" or thank you for signing up" emails?
This sounds like it may be part of a registration bomb attack. I woke up to over 4,000 similar messages a little while back. What they were doing is hiding their actual activity by flooding my inbox. Among the thousands of emails was a notification about the new user added to my PayPal account that had been compromised. That user was trying to empty my bank account.
I caught it before any damage could be done, and the registration bomb ended shortly afterwards.
Actually that did happen at the same time now that you mention it. I managed to catch it quick though. It did happen shortly after midnight. Luckily I’m a night owl and was awake.
How did you find that one email among 4000 sign up confirmations?
It was in the first couple hundred, and I was being selective in what I read. Newsletter and verification emails could be safely ignored, while services I actually have that are attached to my bank accounts get a closer look.
I would contact support and report that address to the police. Other than that check https://haveibeenpwned.com/ and change your password to something unreasonable with >1000 characters or close to the limit of what they allow.
How are that many characters useful? Where is the benefit of 1000, let alone more than that, compared to 50?
With hotmail/outlook, you can tighten up the security a bit, and stop the login attempts.
You can add an alias to you account, and then remove the permission to log in(dont actually remove it completely) from your original email. You will still recieve all the e-mails, and will work like normal, but your sign in will be different.
I had the exact same problem, doing this stopped all the login attempts.
May not apply here but
Note sometimes fraudsters use email bombing when they place orders on an account of yours. They want you to miss the order confirmation/shipping/pickup notifications.
Imagine if they put their brainpower to real jobs
There is nothing you can do about the unsuccessful logins to your email address. My original email address has been in so many hacks and it's always being brute forced by hackers outside the US.
You already have MFA, so the only other thing I can think of is to have an incredibly long random password on your account and make sure the "forgot my password" recovery flows don't have any easy way to bypass. Things like another email address as a backup that's less secure, being able to guess your personal details based on past hacks, easily guessable/researchable security questions (make these random or nonsensical if possible, or don't put details from security questions in social media) could be used to gain access, even with MFA. And finally, secure your password manager in a similar manner.
Password managers such as Bitwarden have password generators that you can use to make on the fly secure passwords (example: gnb*a&2$d9Uzej). You should ideally make the max length that the individual sites supports. Use that for every important account, especially your main email address, especially the one you use for your phone if you are on Android.
Add to this: make sure that your Bitwarden password--or passphrase--is also strong enough to resist attacks. Especially if the email account linked to it is the one that they're trying to break into.
Okay I’ve now switched all my passwords for all my accounts to gnb*a&2$d9Uzej
What now?
Likely that email or a previous email you clicked on was a phishing attack and when you logged in you gave them your password. And if you used that password anywhere else, you let them into those accounts as well. Make sure to check the links in emails are actually pointing to the expected web address and never click through warnings about SSL certificates being invalid. Better yet, never click on email links. Go into your web browser and type in the address manually. And use a password manager with unique, random passwords for every website and use a strong password and a 2FA method that requires access to a physical object or biometrics (cell phone text messages don't count as a physical object). If you still have trouble then it could be that your 2FA method is compromised. If you're using a cell phone, for example, it's possible your neighborhood is the target of a stingray or similar device that mimics a cell tower. Turn off 2G if you can. But even then, that only eliminates a subset of the devices. Get a yubikey or use other, more secure, 2FA methods and be sure to disable the less secure 2FA methods, because you're only as secure as the least secure one.
Like others have said, change your passwords, activate 2FA if available, never reuse passwords etc, etc, etc.
I have been getting repeated warnings for unsuccessful logins to my Microsoft account for some time now. I'm guessing some bad actors are just throwing whatever leaked passwords they have hoping for hits. I have 2FA turned on and a password complex enough to deter dictionary attacks, so I'm not really concerned.
Whats a dictionary attack? I've never heard that term before
Basically, guessing lots of passwords from a list (dictionary): https://en.wikipedia.org/wiki/Dictionary_attack
Well I feel dumb, lol it seems obvious now that you said it
Don't feel dumb, asking questions and reading is how we learn.
I've had the same Microsoft ones for years now. At least once a week there'll be a block of 10 - 20 of those emails. Guess they still haven't succeeded!
I am currently using the iOS password manager. I have my qualms with it but it’s been mostly pretty solid. I was an android user for years and used a fair share of password managers, I like the iOS one the best but I know some of the new managers are much better. I don’t know any other iOS compatible password managers. I’m open to suggestions.
Also every account that uses 2FA has either an Authenticator code or email to an authentication secured email address.
bitwarden. don't repeat passwords. setup mfa on things you haven't already. that's about it. new, random password for each account.
sounds like one was compromised so they're doing a password spray on everything they can find. passwords like BD!CzuX0$Wemt2 will never be brute forced or randomly guessed, they're usually stolen in data breaches, but if all passwords are different and not repeated, you're doing everything you can.
"hacks" happen, you can minimize by using different passwords on each account, use bitwarden to generate and save them.
Was the password on macys randomly generated? Or do you think that could have been the same password as another website?
After logging into Macy’s I got 43 emails at once to seven different services like “Excalidraw” and “Sportograf” trying to login using a magic link.
If you never use this kind of signin method, I'd make a rule to automatically delete those emails with the magic link so that you don't accidentally use them.
Other than that, a secure password and 2FA are your best defenses.
First, same advice as everyone else. Change your passwords. Password managers are great. I like keepass.
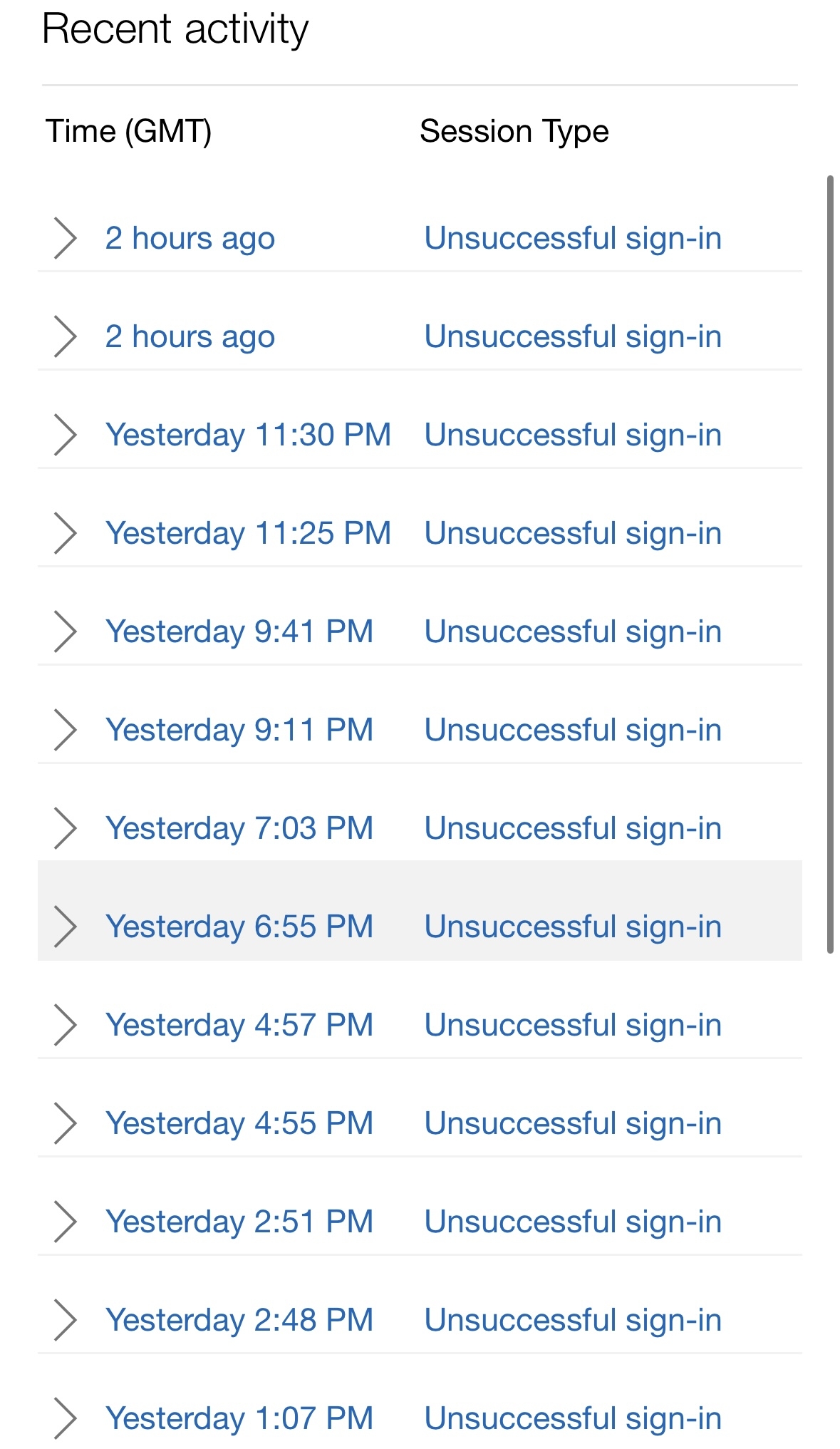
Regarding the email, this looks like a Hotmail/Microsoft/Outlook account. Their security page sucks ass. It lists every time someone unsuccessfully tries to log in. "Unsuccessfully" as in they tried your email with an incorrect password. Of course hackers are going to try to break into your account. You really only need to worry about successful logins that aren't you.