the_dunk_tank
It's the dunk tank.
This is where you come to post big-brained hot takes by chuds, libs, or even fellow leftists, and tear them to itty-bitty pieces with precision dunkstrikes.
Rule 1: All posts must include links to the subject matter, and no identifying information should be redacted.
Rule 2: If your source is a reactionary website, please use archive.is instead of linking directly.
Rule 3: No sectarianism.
Rule 4: TERF/SWERFs Not Welcome
Rule 5: No ableism of any kind (that includes stuff like libt*rd)
Rule 6: Do not post fellow hexbears.
Rule 7: Do not individually target other instances' admins or moderators.
Rule 8: The subject of a post cannot be low hanging fruit, that is comments/posts made by a private person that have low amount of upvotes/likes/views. Comments/Posts made on other instances that are accessible from hexbear are an exception to this. Posts that do not meet this requirement can be posted to !shitreactionariessay@lemmygrad.ml
Rule 9: if you post ironic rage bait im going to make a personal visit to your house to make sure you never make this mistake again
view the rest of the comments

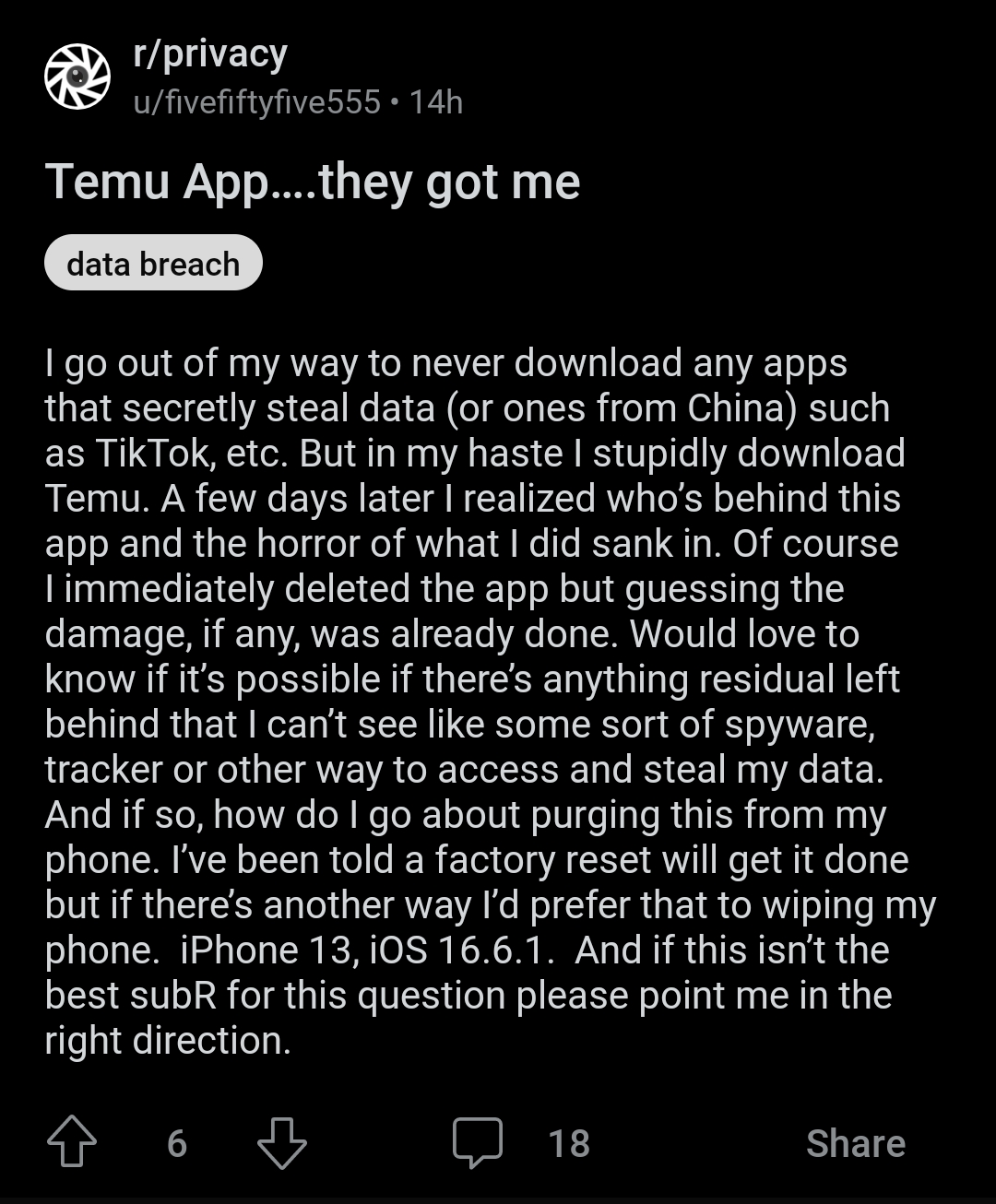
To be clear, it is possible to defend yourself, but ofc no defense is perfect. For illegal activities that might attract federal attention? best to avoid them at all costs. But for general privacy in your day to day life that isn't practical for most people, and "every cellphone is snitching on you" is way too reductive, even if it's true in a sense.
For example the person you are replying to mentions Linux phones, many of which publish schematics and make hardware kill switches for the discrete modem a big selling point. That still isn't perfect protection, but it would protect you from a stingray... and if you have a thought out threat model, you can make the choice whether or not that device is appropriate for your situation.
Let me be clear first: If you want to get rid of advertising, then yes your advise is OK. If you want to defend against the Surveillance system, it's not close to adequate. This is the fundamental gap I'm trying to address.
I understand where your heart is at, but you are making a mistake. Free/Libre software is about Freedom, and from that guarantee we can build other guarantees about security and privacy. However Freedom itself does not guarantee security nor privacy. Freedom is also the freedom to shoot yourself in the foot.
There is a perfect defense: Don't use technology. Much of this advise is trying to use technology to fight technology. It's a rabbit hole that has no bottom, and the best defense is to not play. The problem is attack surface. Technology is incredibly complex and is chattier than your extroverted :LIB: friend at brunch, and boy howdy do people love to listen! You can reduce this attack surface, but it never goes away as long as you are using technology.
do people love to listen! You can reduce this attack surface, but it never goes away as long as you are using technology.
Here's the trail crumbs you might make on the Web as you browse each and every website:
You can use custom software for #3 and #4 on the device (most of the advise here), but do you block google.com? You can use a network DNS blocker (e.g. Pi-Hole) for #1, #3, #4, and some of #7, but that only works on networks you control. VPNs advertise as solving #2, but that's pure ideology; it only moves where the routing traffic goes and still can log information in transit.
This also ignores data brokers who buy all of this information and compile it together.
And this is just the advertising/surveillance defense against tech companies. I haven't even touched or
or  defense.
defense.
if your threat is state-level actors your computer security is approximately moot and maybe you should spend your money on laywers and having a discreet way out of the country
That's not necessarily true. Police are purchasers of this data from data brokers. It's state surveillance without any need for a warrant.